This will be a weird and fun post.
I have recently been working with Autonomous Database migrations and wanted to highlight the option of using Oracle datapump (ZDM Logical Offline) and network link option.
Using network link removes the need to export the data first to cloud storage and allows you to import “directly” your data. There are some considerations when using network link, which I will go through on part 2.
This part 1 will be all about setting up the networking between source database network and Google Cloud Autonomous VPC. The only way currently to provision your Autonomous Database on GCP is with a private endpoint, this means that where ever your source database is, two things need to happen:
- You will need to have private connectivity and routing from source network to GCP VPC
- You want to be able to resolve the private Autonomous endpoint FQDN from the source network and you want to resolve source database FQDN from the Autonomous network from the GCP side
In my example, my source database is running on OCI Toronto region (ca-toronto-1). My Autonomous database is running on GCP us-east-4 region where the overlay network on OCI is created in OCI us-ashburn-1 region.
Remember, the Autonomous database runs inside GCP region, due to way how it’s implemented, there is always some networking resources and the actual Autonomous Database visible in the OCI Console, where you can also manage these resources.
Setting Up Connectivity
For the initial connectivity, I’ve build IPSec VPN Tunnel between OCI and GCP. Luckily the whole process is documented very clearly.
You can find the IPSec VPN connectivity guide from here: https://docs.oracle.com/en-us/iaas/Content/Network/Tasks/vpn_to_gcp.htm
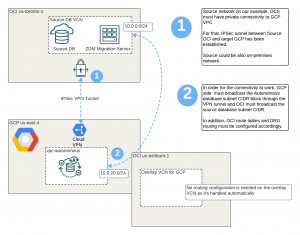
From above diagram, you can see the requirement to build the tunnel and also set up the routing. You should check what is being advertised from both sides of the connectivity.
For GCP (below), I did have to add the Autonomous Subnet manually as advertised route.

On the OCI side I see the same routes received, you should check also the advertised routes.

On the OCI side, you want to make sure from the VCN you have a route towards DRG and DRG route table has a route towards IPSec VPN tunnel. When I go to DRG route table for VCN attachments and see all routes, I can see the IPSec VPN routes coming up from there.

Setting up DNS
Now that I have connectivity, I want to be able to resolve the necessary hostnames/FQDNs. I will need to be able to resolve the source and target from the ZDM server as well as there needs to be connectivity from Autonomous DB to Source DB when I create and use database link (for the network link option).
Depending where you would have ZDM server, it might change some parts of the diagram below.
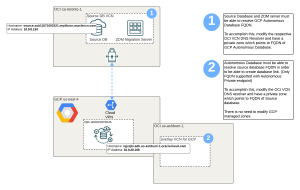
What does above diagram tell us? You have source FQDN on ca-toronto-1 region and target ADB on GCP us-east-4. The nice thing with Google is that they do all the initial DNS setup automatically. So, you can resolve Autonomous FQDN within the GCP VPC without any work!
Source DNS
For the source network side, I’ve done it with minimal effort. Each OCI VCN has a DNS resolver and when you go to the resolver, you can modify the private view and zones associated on the views. For this test, I’ve added just A record on the Zone which is associated on the respective view on the resolver.
I could have also done a forwarder towards the GCP resolver.
I do have some older posts on it if you want to drill down on them:
When I go to my resolver, I see the associated private view.

And when I drill down the the private view, I can see zone which I’ve added for the Autonomous. This way, when I resolve addresses on my source VCN, it will know Autonomous hostname points to a specific IP which then is running on GCP VPC.

That takes care of the source side DNS. Now we’ll do the Autonomous side.
Autonomous DNS
For Autonomous, we will need to be able to resolve DNS so we can create the database link. Typically folks will tell you that there is no need to do anything on the OCI side, in this case there is! Autonomous database resolves hosts from the OCI DNS resolver, not from GCP!
In this case, we will need to create NEW private view on the linked multicloud OCI tenancy which is where you see Autonomous Database running as well. When you provision your Autonomous Database from GCP Console, OCI automatically creates multicloud VCN on the OCI side (I call it overlay VCN) which is where Autonomous “runs” too.
On this VCN, there is no private view associated, so we will just create view, with a zone and that zone has necessary domain and A record towards our source database.


And that’s it for the Autonomous piece! Now when I create DB link (shown in the next post) I can also connect to the source database.
Summary
Now I have established connectivity from my source database to autonomous database as well as can resolve the hostnames with source and target.
Remember the Autonomous Database on GCP is a private endpoint, so you always need to resolve that from the private network, not from public! This sometimes makes the setup more complex what you would might think is needed.
In the next post, I’ll drill down on the ZDM migration with network link!