As you might have seen, few weeks ago Oracle announced improved Dynamic Routing Gateway functionality which I was super excited about. Why? Previously when you’ve designed Transit Networking on OCI you’ve always had to use Hub & Spoke model for your traffic to flow from on-premises to Spoke VCN. Also, setting up connectivity between VCNs…
OCI Transit Networking DNS part 2 – Custom DNS options
We looked on setting up Oracle DNS on part 1, and how you could manage different DNS options with Private Views or DNS listeners & forwarders. In this post I’m gonna look on what options we might have with Custom DNS. Custom DNS is typically used when there’s a requirement to use already existing DNS…
OCI Transit Networking DNS part 1
First of all, big thanks for my colleagues Rob and Travis for giving me some good ideas on this post! I usually recommend Transit Networking for most of the implementations as it provides security and scalability for your OCI infrastructure. Transit networking means one of your VCN acts as a Hub and the other VCNs…
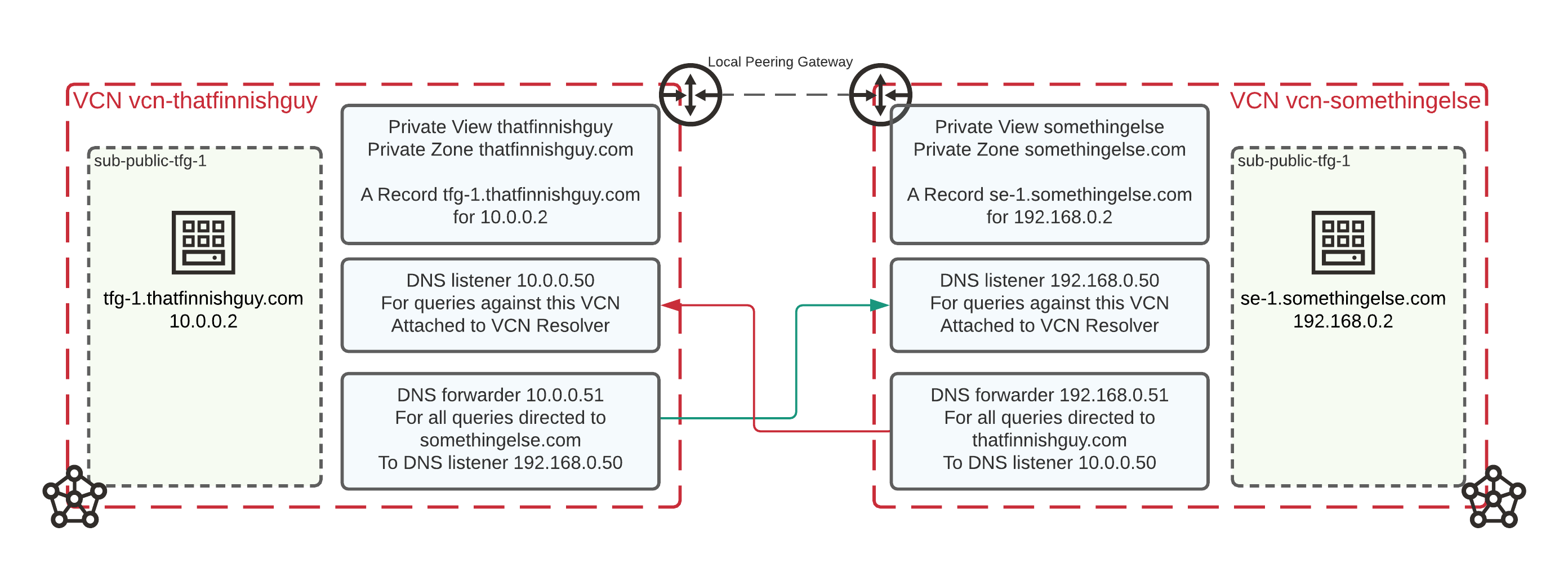
OCI Private DNS part 2 – DNS forwarders and listeners
This is the second part of my OCI Private DNS posts. You can read the first part from here. In this post I will extend my configuration to have two VCN’s which will be connected via Local Peering Gateways together. Other VCN will have Private Zone for thatfinnishguy.com and the other VCN for somethingelse.com. Both…
OCI Private DNS part 1 – Configuration
I’ve wanted to write something about this topic for quite a while and finally OCI has released it’s first step of Private DNS capabilities! Why do I think this is a big thing? For example let’s say you need to have Hub & Spoke model with multiple VCNs, if you’ve wanted to resolve hostnames between…
Use case for Network Security Groups in OCI
So a while back OCI got NSGs (Network Security Groups) but most what I still see with implementations is that people tend to use Security Lists. Remember Security Lists are applied on subnet level while NSGs are applied to VNICs. I recently got following dilemma on tenancy created a while back. Challenge All the subnets…
Series – Get your database running with Terraform part 6: Security Lists
Before we can create the subnets we still need to create security lists. They will control what ingress and egress traffic will be allowed within subnets. I will create two security lists for this project, one for private subnet and another one for public subnet. Security lists can have have multiple rules in them and…
Series – Get your database running with Terraform part 4: IGW and NAT GW
Previous part three on creating VCN can be found from here. Now let’s start with basics. What are IGW and NAT GW. Internet Gateway (IGW) in OCI is the connection point which routes your VCN traffic from and to public Internet depending on what traffic you allow through your security lists. If you use an…